Managing Windows Virtual Desktop with Microsoft Endpoint Manager - Part 2 - Enrolling your WVD session host into Intune
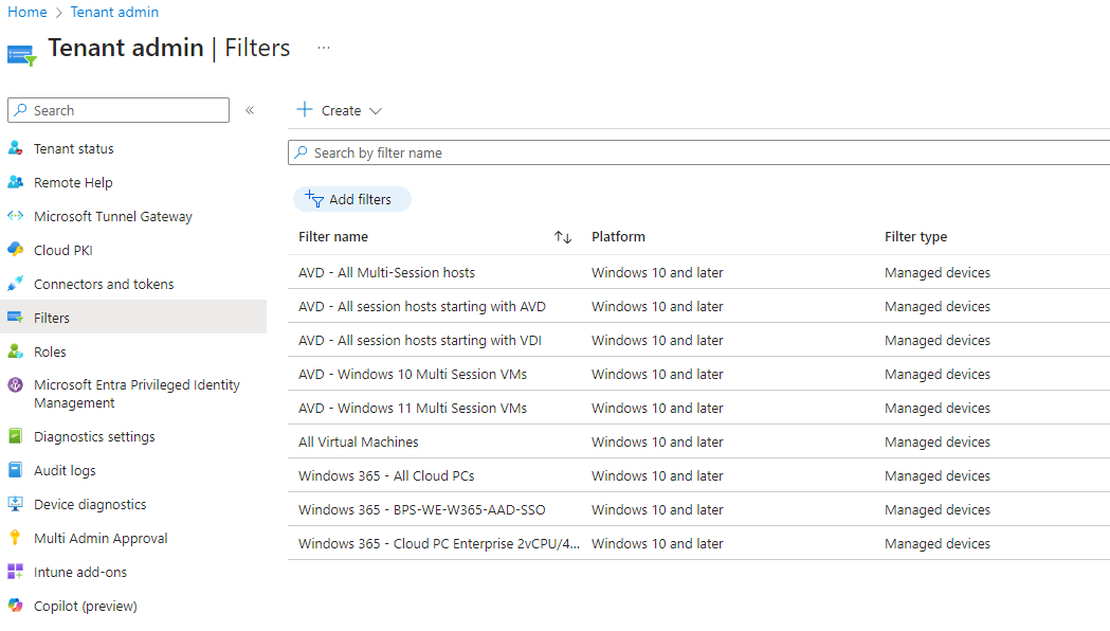
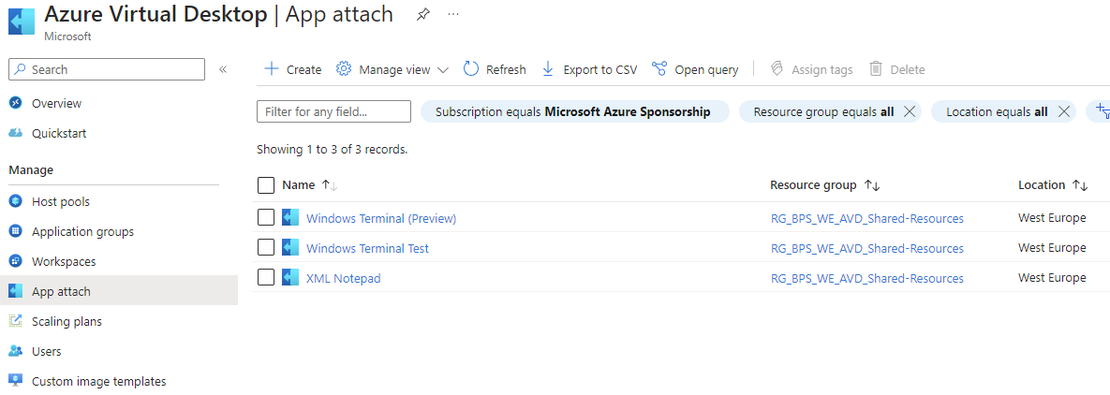
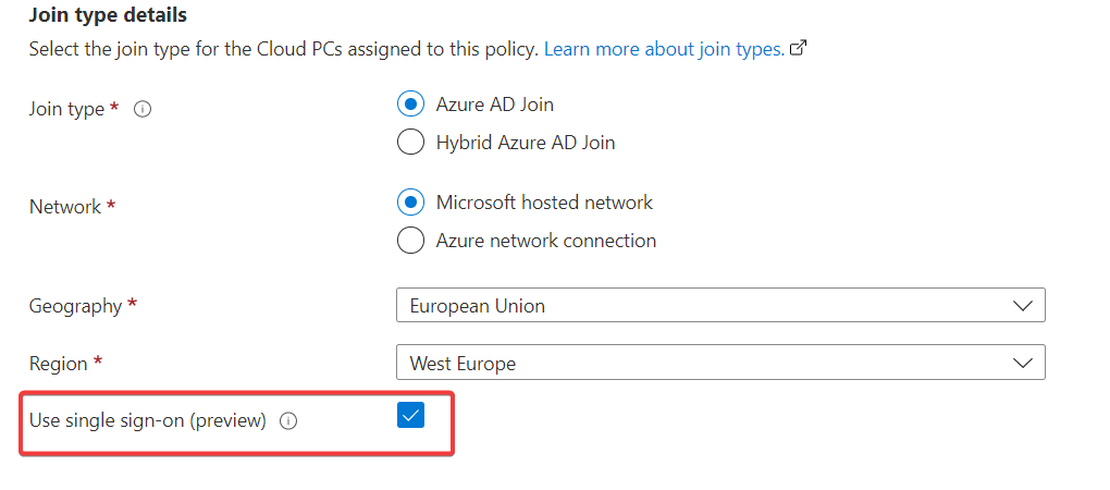
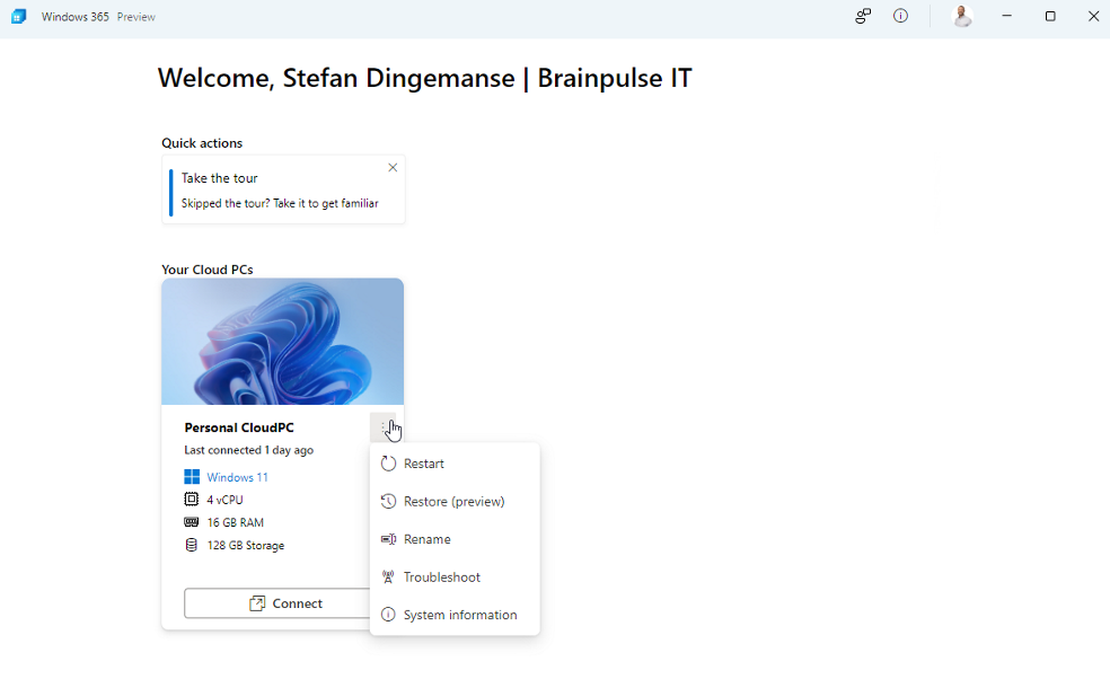
This is the second part in the Managing Windows Virtual Desktop with Microsoft Endpoint Manager series. In the previous part I showed you how to join …
Continue Reading