Simplify Virtual Desktop Management with Intune Filters for Windows 365 and AVD
Are you considering managing your virtual desktops (Windows 365 and Azure Virtual Desktop) with Intune? There are several reason to do so. One of the key benefits of using Intune to manage your virtual desktops is the ability to leverage the power of the cloud to streamline and simplify the management. Probally you are already using Intune to manage your physical endpoints, meaning you already have configurations, policies and applications in place. This could result in these configurations being applied to your virtual desktops.
I am a big fan of keeping things simple, deploying configurations as a baseline to all users or all devices and create specific configurations for specific use cases. This approach could lead to configurations which are not supported on for example a Multi-Session OS, or for example compliance policies which requires BitLocker on your Cloud PCs.
If you want more control you could leverage using Dynamic Groups or Intune Filters. This post is about using Intune Filters and using them for Windows 365 and Azure Virtual Desktop.
Table Of Contents
What are Intune Filters?
Intune filters are a powerful feature that allows you to target specific devices or users when assigning policies, profiles, and apps. With filters, you can narrow the scope of your assignments based on rules you create. For example, you can use filters to target devices with a specific OS version or manufacturer, or to target only personal or organization-owned devices. This added flexibility helps you to keep your environment reliable and efficient. Filters can be used in combination with group assignments to achieve the desired targeting outcome.
Simple said, filters allows you to narrow down the assignment of policies and configurations.
Using Intune Filters for Windows 365 and AVD
As already mentoined, if you are starting with Windows 365 or migrating your current AVD environment to a more modern approach where you will leverage Intune to manage those virtual endpoints.
Regarding Windows 10/Windows 11 bassically almost everything has support for filters. There are a few exceptions:
- Wired network
- Attack Surface Reduction (Excludes Web protection (Microsoft Edge Legacy), Application control, and App and browser isolation)
- Security baselines
- Custom compliance policies for Windows 10/11
- PowerShell scripts for Windows
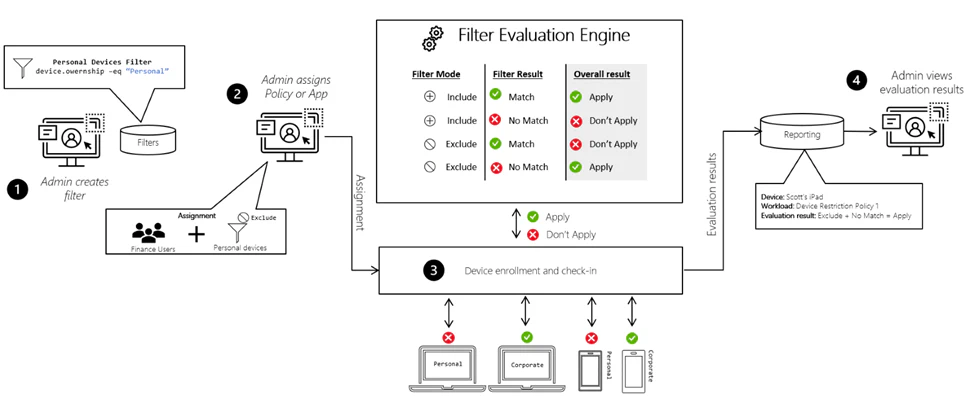
As you can see in the image below filters are evaluated when policies are applied to endpoints. Based on the filter mode and the filter result your policies will be applied (or not).
Examples
Below there are a few examples to get your started using filters for Windows 365 and Azure Virtual Desktop
Windows 365
| Name | Rule Syntax | Result |
|---|---|---|
| Windows 365 - All Cloud PCs | (device.model -contains “Cloud PC”) | All Cloud PCs |
| Windows 365 - All Sales Cloud PCs | (device.enrollmentProfileName -eq “BPS-WE-W365-Sales”) | All Cloud PCs from a specific provisioning policy |
| Windows 365 - All 2vCPU/4GB RAM Cloud PCs | (device.model -contains “Cloud PC Enterprise 2vCPU/4GB/64GB”) | All Cloud PCs with a specific configuration |
Azure Virtual Desktop
| Name | Rule Syntax | Result |
|---|---|---|
| All Virtual Machines | (device.model -startsWith “Virtual”) | All Virtual Machines including AVD |
| AVD - All Multi-Session hosts | (device.operatingSystemSKU -eq “ServerRdsh”) | All Multi-Session hosts |
| AVD - All W10 Multi-Session hosts | (device.operatingSystemSKU -eq “ServerRdsh”) and (device.deviceOSVersion -startsWith “10.0.1”) | All Windows 10 based Multi-Session hosts |
| AVD - All W11 Multi-Session hosts | (device.operatingSystemSKU -eq “ServerRdsh”) and (device.deviceOSVersion -startsWith “10.0.2”) | All Windows 10 based Multi-Session hosts |
| AVD - All session hosts starting with AVD | (device.deviceName -startsWith “AVD”) | All devices starting with AVD |
| AVD - All session hosts starting with VDI | (device.deviceName -startsWith “VDI”) | All devices starting with VDI |
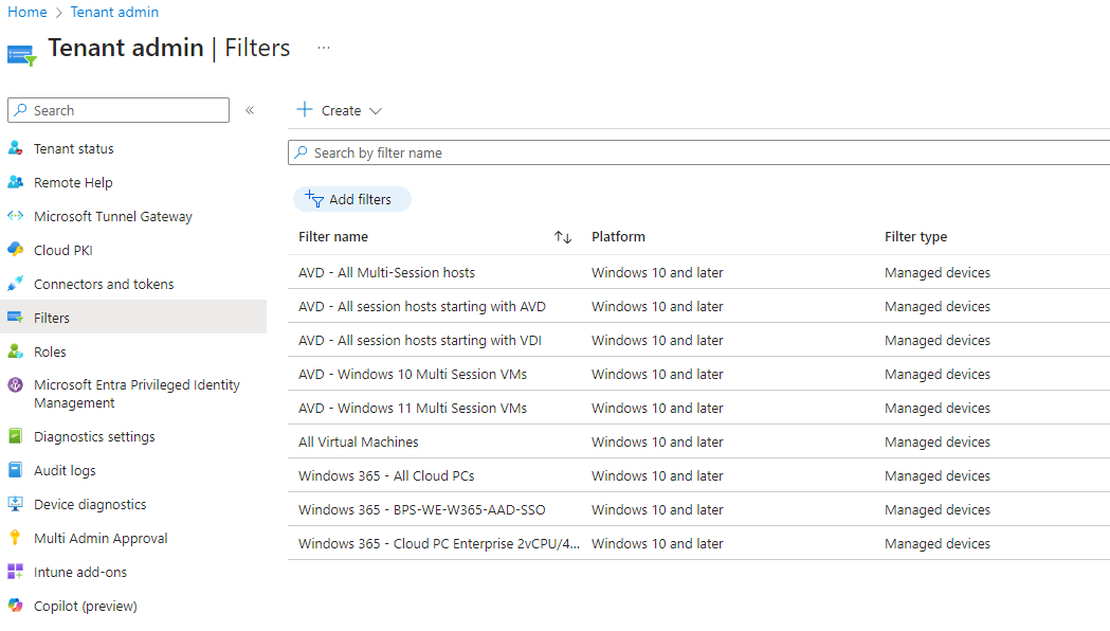
These are all ready to go filters to get you started.
Creating filters
If you didn’t have used filters before I will show you how to quickly create them and use them in your environment.
- Navigate to your Intune management portal and select Tenant administration > Filters
- Select Create and choose Managed Device
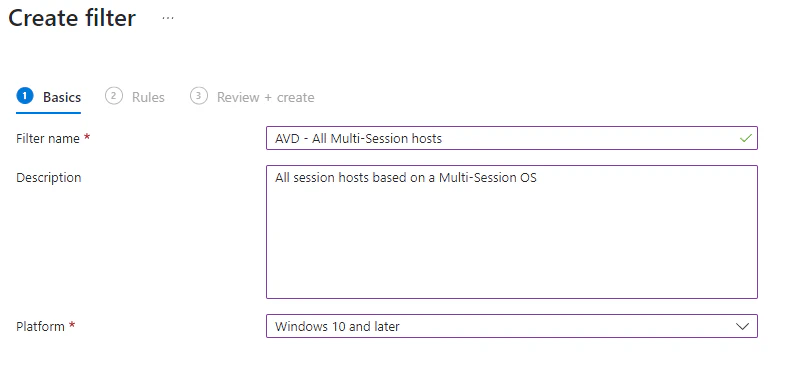
- In the Basics tab, enter the required properties
- Filter name: Enter the name of the filter
- Description: Enter a clear description of what this filter will be filtering
- Platform: Select the platform and choose Windows 10 and later
Now it’s time to create the rules. Within the Intune portal you will have two option, you can create the rules with the rule builder or create it with the rule syntax box. The rule builder is the easiest way so let’s use that one so let’s continue.
- Within the rule builder select the property operatingSystemSKU (Operating System SKU), the operator Equals and for the value select ServerRdsh
(device.operatingSystemSKU -eq “ServerRdsh”)
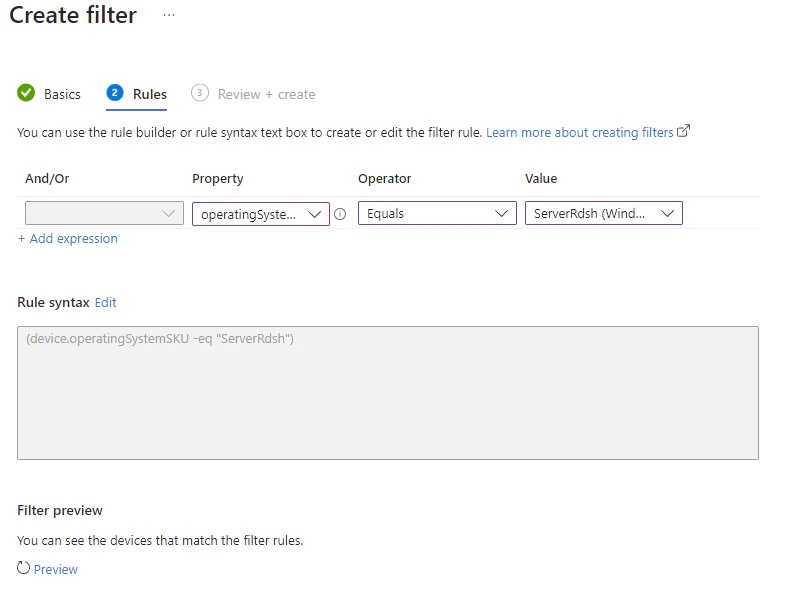
During the creation of a filter (and later when editing the syntax) you will be able to validate if the correct endpoints will be picked up with the create filter.
- Click on Preview and validate the results.
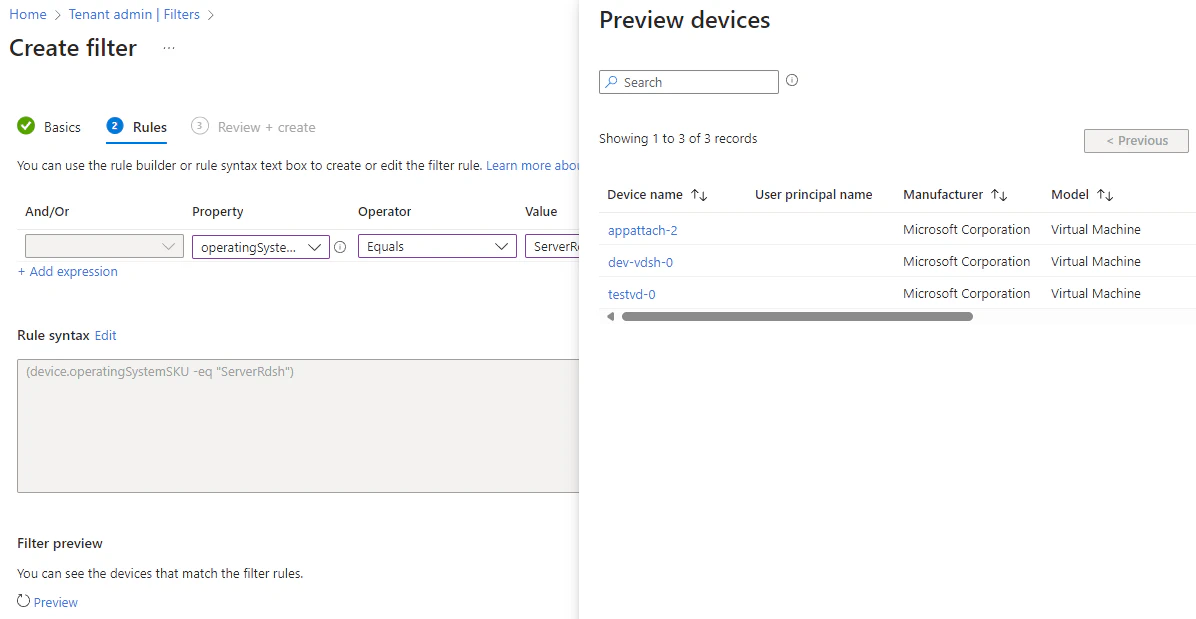
- When ready, click on Next. Now it’s time to review the settings and hit Create. After the filter has been saved it will show up in the filters overview
Using Filters
When you have created a filter you can now use it when assigning policies or apps..
Best Practices
Here are some best practices for using Intune filters:
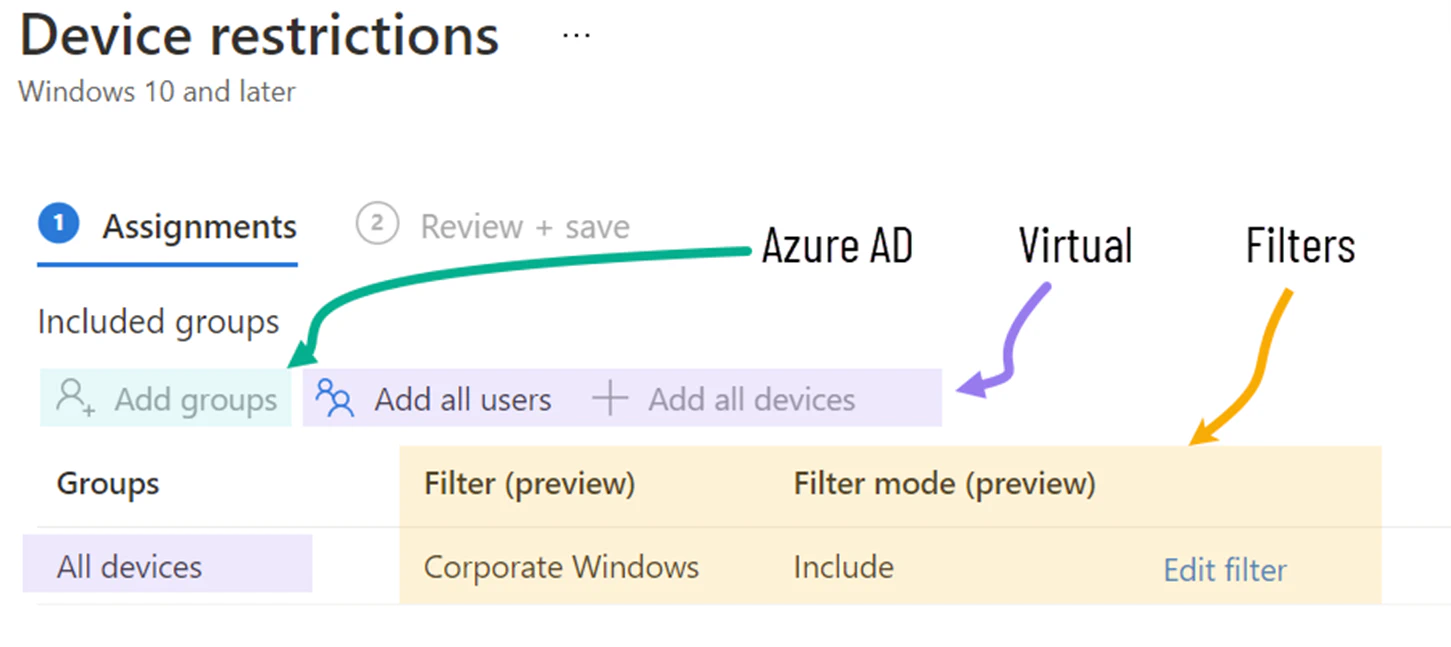
- Use groups or virtual groups, and apply filters to help refine the targeting scope.
- Don’t create your own version of “All users” or “All devices” groups. Use the Intune virtual groups, as they don’t require Microsoft Entra ID syncing when a new user or device is added to the environment.
- Re-use groups to optimize your targeting. Make incremental group changes for more efficient processing.
Conclusion
Intune filters are a powerful functionality within Intune that can help you simplify the management of virtual desktops using Windows 365 and Azure Virtual Desktop. By using filters, you can target specific devices or users when assigning policies, profiles, and apps, helping you to keep your environment reliable and efficient.
Sources
MSIX app attach and app attach - Azure Virtual Desktop | Microsoft Learn